Enterprise Data Security
Keep your data secure for Integration and AI.
Keep your data secure for Integration and AI.
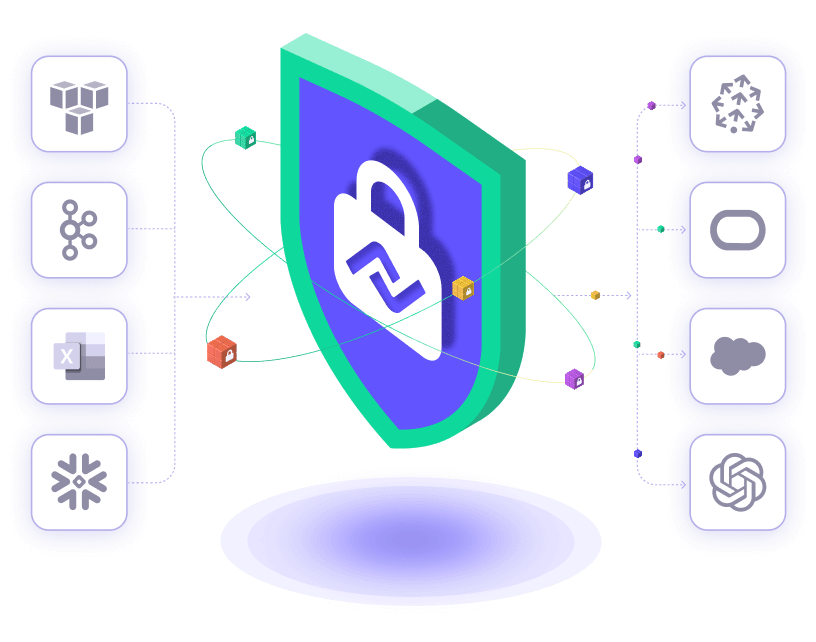
Encrypt data at rest and in motion for complete end-to-end security. Every entity in Nexla – Nexsets, flows, transforms, and credentials – has fine grained access control.
Easily integrate with leading SAML or OIDC-based single sign-on systems including Auth0, Okta, OneLogin, ID Anywhere, and Microsoft Active Directory.
Deploy Nexla in the cloud, hybrid multi-cloud, or completely on premises so that data never leaves your environment. Nexla ensures you can safely secure every combination.
Nexla ensures that each connector or API call secures the connection and uses the native authentication and authorization. Each connector on the Nexla platform is individually authenticated using protocols like TLS1.2, SSH-2, and IPSec. For APIs, Nexus supports most API authentication mechanisms including Oauth, HMAC, and JWT as well as basic and header-based authentication.
Protect personal identification information (PII) from access using policies like data hashing. For example, Nexla’s built-in hashing uses 256-bit SHA strings to mask sensitive user information from consumers. You can quickly add your own algorithms as custom validation policies and apply them across different sources.

Nexla doesn’t store any data records, and you have complete control over what is seen. Nexla first enforces validation policies on data, which can include redacting or obfuscating any sensitive data. Also, only a part of the data is sampled. Administrators can control all access based on user requirements and permissions.
The choice of running your data processing in a regional infrastructure is entirely yours. All secure mechanisms of connectivity to your internal systems are supported including SSH, VPN, or Bastion host.
Nexla ensures all security credentials are protected from everyone. You can use Nexla’s built-in credential vaulting, or if you’re a Nexla Enterprise customer you can also bring your own vaulting mechanism.
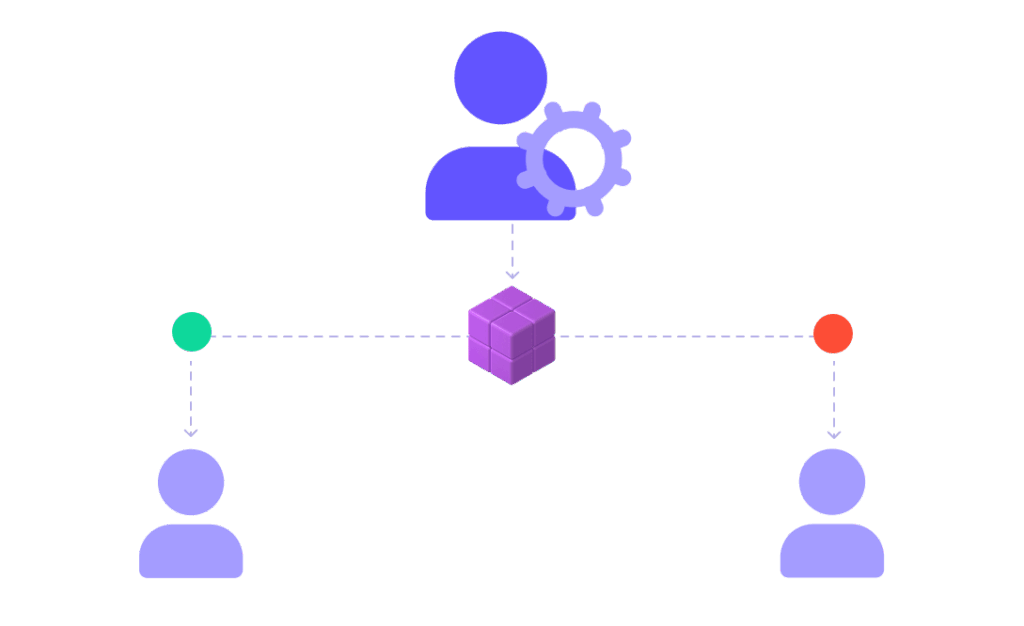
See complete end-to-end lineage and access log down to individual records to help verify access by the right people or troubleshoot potential hacks. Nexla also lets administrators quickly add or revoke access at any time to help maximize security and promote collaboration.
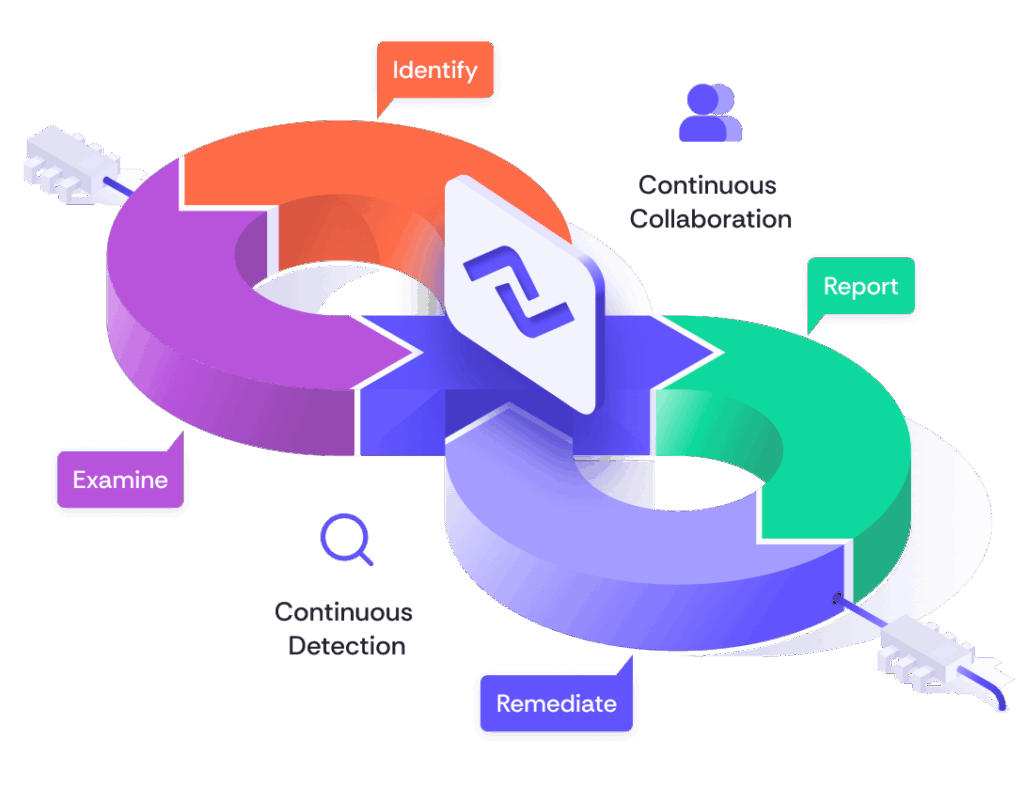
Nexla implements continuous security testing to identify, examine, report, and remediate any security issues. This includes continuous container scans, code scans, and routine penetration tests by independent security experts to help achieve a state of zero vulnerabilities.
Nexla continues to meet the most stringent standards of security with SOC 2 Type II compliance with the highest security, confidentiality, availability, and privacy controls based on criteria defined by AICPA (American Institute of Certified Public Accountants).

Nexla is fully compliant with the European Unions’ Global Data Protection Regulation, or GDPR, and California Consumer Privacy Act (CCPA). Nexla makes no copies of your data as it ingests, processes, and delivers the data to your users and applications.
