Event Stream Processing
Transform and integrate real-time streaming data with SaaS, apps, databases, storage, batch, and more.
Transform, enrich, and integrate any streaming data for all your AI, analytics, operations projects using a graphical UI or natural language prompts powered by AI, without having to write code or manage the complexities of stream processing.
Convert files or batch processes to event streams and vice versa without having to worry about the details. Nexla automatically turns streaming data and other sources into data products using metadata intelligence that are format, protocol, and speed-independent.
Integrate streaming with anything at any speed using 100s of universal bidirectional connectors for streaming data, databases, data warehouses, SaaS, legacy apps, APIs, webhooks,files, storage, and more.
Nexla connects to popular event stream processing sources and destinations to support end-to-end heterogenous streaming, including:
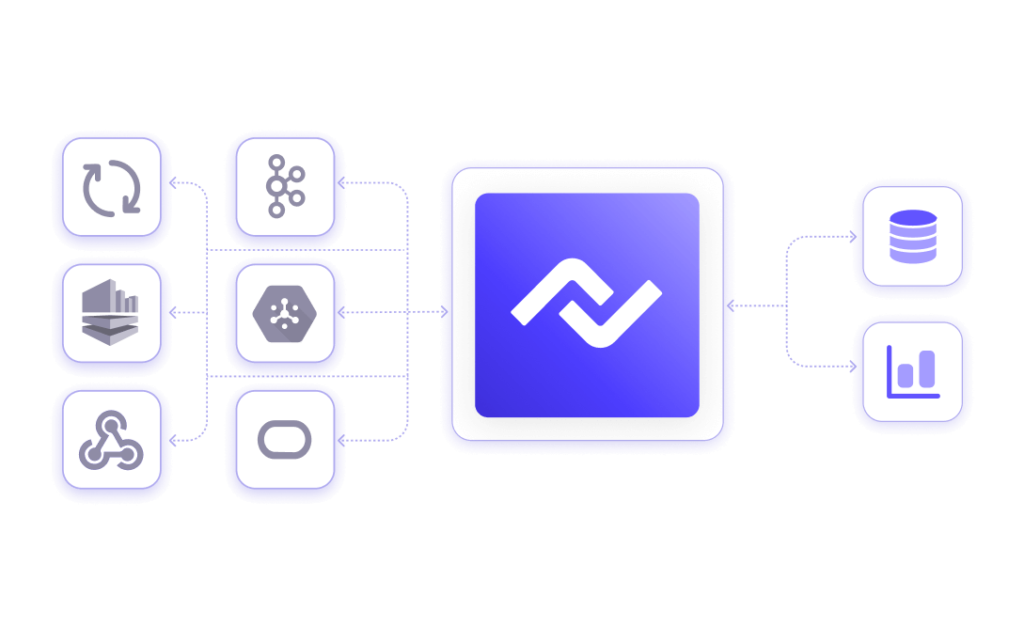
When Nexla connects to each source, including streaming data platforms, it automatically converts topics or queues into data products using metadata intelligence powered by AI. All data products are independent of formats, protocols, and speed. It means you can easily work with streams without all the complexity of other stream processing technologies.
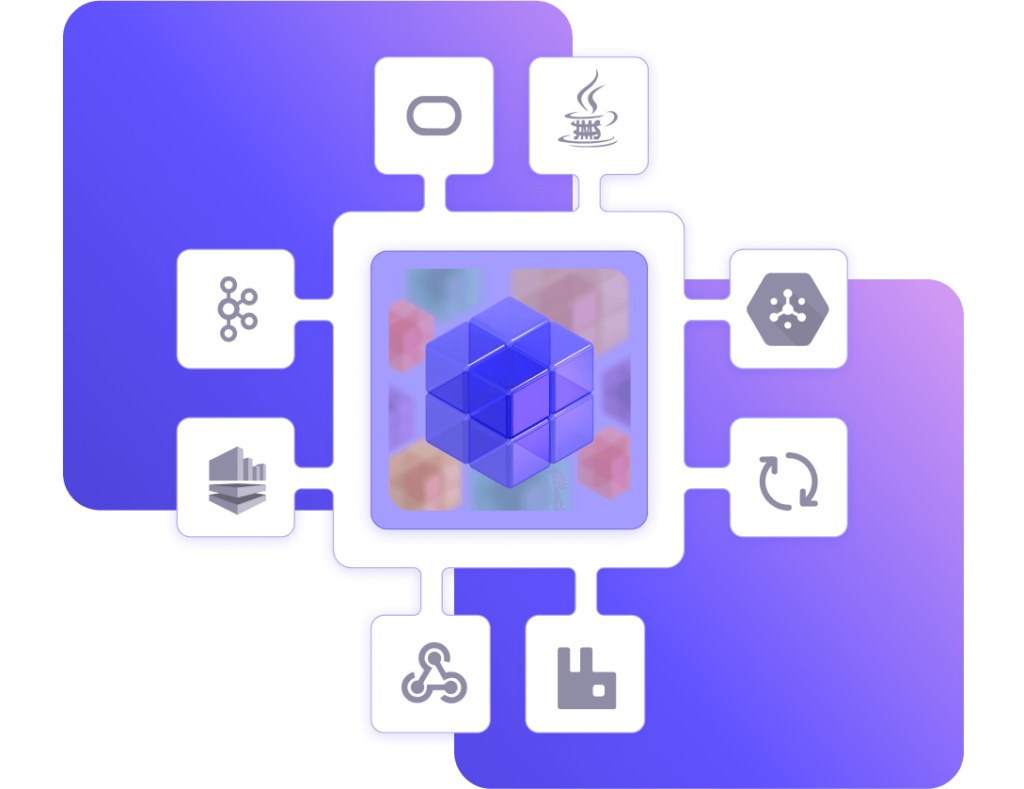
Once your streaming data is accessible as data products, you can reuse it anywhere for AI, analytics, operations, even customer and partner integration. Transform and combine streaming data with any other real-time or batch data using any integration style, all without coding.
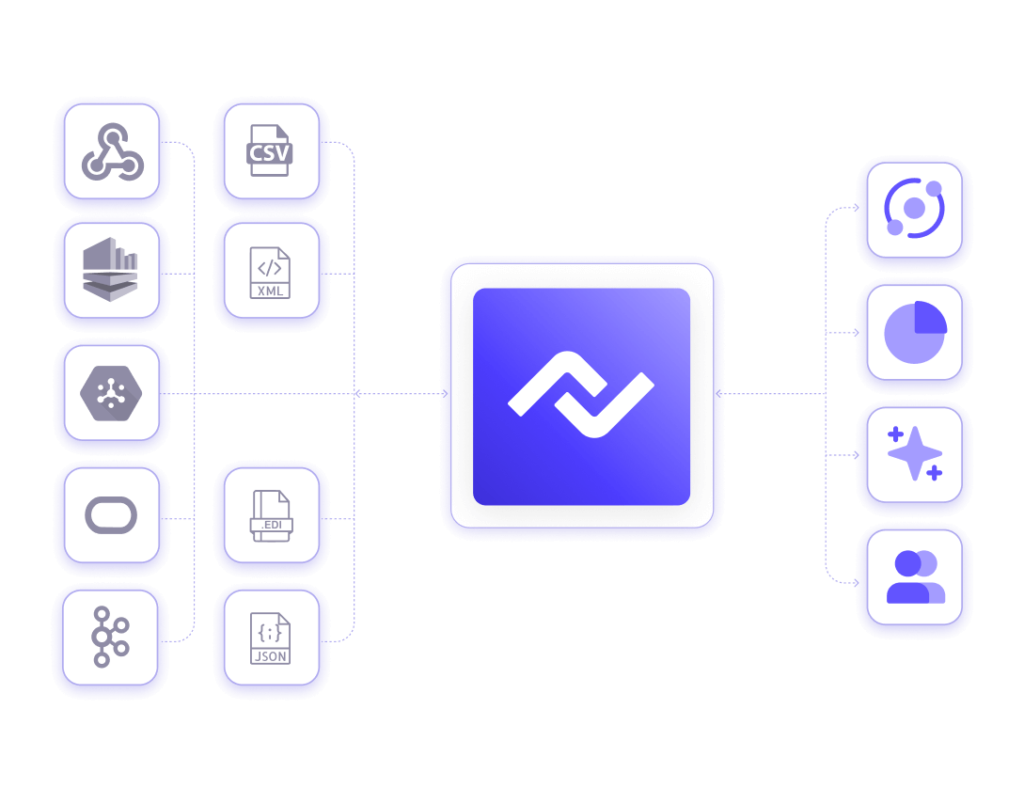
Nexla provides built-in end-to-end DataOps and monitoring for all flows, including stream processing. It validates schema and data, detecting questionable data or schema changes as they occur and alerting you instantly. Nexla automatically propagates non-breaking changes and allows you to automate data quality and schema evolution, minimizing downtime.
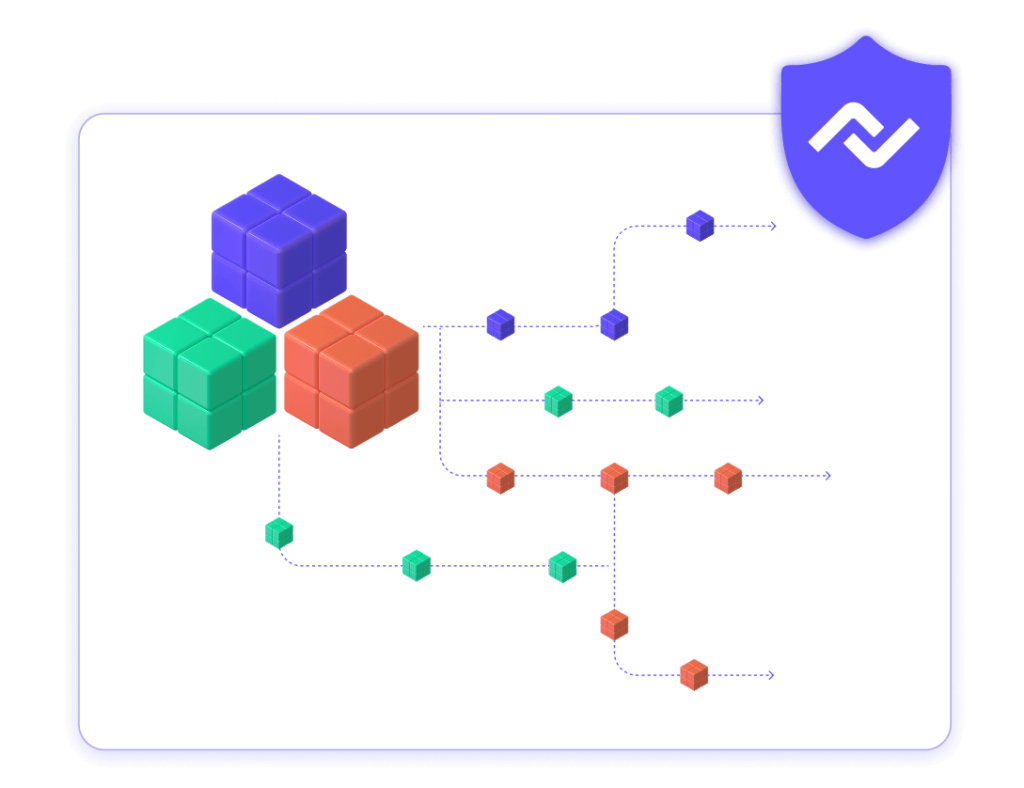
Nexla’s built-in encryption, hashing, and anonymization makes it easy to control exactly which attributes you send to internal systems or share with external partners. Built-in transformations make it easy to hash or mask any PII (personally identifiable information) with a few clicks. All data is transformed mid-stream in real-time. End-to-end data encryption keeps all event stream processing secure.
